After the onset of the coronavirus pandemic, as more companies shifted to remote work, cybercriminals took advantage. The number of reported cybercrimes more than tripled compared to before the pandemic, according to the FBI.
Small businesses are attractive cyberattack targets. Many smaller companies lack the IT knowledge to execute effective online protections.
Fortunately, organizations can turn to a virtual private network (VPN) to prevent cyberattacks. VPN technology has existed for years. Now, it’s easier than ever to implement a VPN.
Overview: What is a VPN?
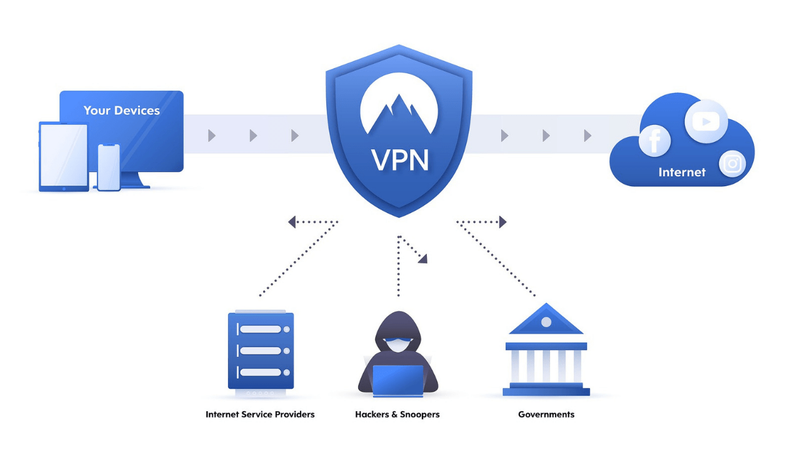
When you use the internet, you’re sending and receiving data over a public computer network. Without security in place, a cybercriminal can spy on you unnoticed, seeing which websites you’re visiting, who you’re exchanging messages with, and even steal sensitive data, such as your bank login.
A VPN turns a public internet connection into your own private network. It routes your online messages through a VPN server before sending them to their destination.
It works like this:
• You install VPN software on your digital devices, such as laptops, mobile phones, and tablets, collectively called endpoints. This software encrypts your data and creates a secure connection, called a tunnel, between your device and the VPN server. This prevents cybercriminals from accessing your data.
• When your encrypted internet traffic arrives at the VPN server, it’s decrypted and assigned the internet protocol (IP) address of the server before it’s sent to the website or person you’re communicating with online.
The VPN’s secure tunnel ensures a criminal cannot hack into your internet connection. Since your data is encrypted and the VPN masks your IP address, your identity is private.
With these benefits, it’s no wonder VPNs have been widely used by large companies for years. VPN providers now make the technology accessible to small businesses.
Let’s look at how you can set up a VPN for your organization.
How to set up a VPN
If you’re a large business with many employees and an IT department, you can set up your own VPN using cloud-based technology provided by vendors such as Amazon Web Services. Or you can buy your own servers.
If you’re a smaller business or lack an IT department, your best bet is to subscribe to a VPN service provided by a third party. Many companies offer VPN services, from internet service providers (ISPs) such as AT&T to endpoint security firms, for example, NortonLifeLock.
Since many small businesses lack the expertise to build their own VPN, we’ll walk through the steps to set up a VPN through a VPN service provider.
1. Initial prep
The first step to VPN setup is to evaluate your needs and gather the necessary components. Here are questions to consider.
• How many and what kinds of devices need a VPN?
• Which computer operating systems (OS) are you using? VPN vendors provide support for popular OS such as Windows, but not all do so for an OS such as Linux.
• Do you need VPN protection for staff in different locations?
• What kind of VPN protocol do you need? See the next step for details.
• Will you need to upgrade your internet connection speeds? A VPN will slow down your online activities. So if you already feel like your connection could use a boost, get one before adding a VPN.
This initial assessment helps you find a VPN vendor who can meet your needs. Some VPN vendors also offer endpoint security software.
A VPN requires equipment as well: a router, server, and software specifically designed for a VPN.
• When you choose a VPN service through a vendor, they’ll provide the VPN servers and software.
• A standard router typically works fine with a VPN, which is good news for remote workers. But if you’re setting up a company IT network in a shared space, such as an office, it’s better to use a VPN router. Multiple staff will connect to and use the internet provided by the same router, and a VPN router is more secure.
2. VPN protocols
One VPN consideration can prove confusing to the uninitiated: VPN protocols. Vendors offer different VPN protocol options, so this attribute can affect the vendor you choose.
VPN protocols are a set of instructions that control how data flows between your device and the VPN server. They determine details such as the speed of your connection and the level of encryption used on your data.
Several VPN protocols exist, each with pros and cons. A VPN provider may not offer all protocols, so if there’s one you want, ask before signing up with the vendor.
Some of the most prevalent protocols include the following.
• OpenVPN: This is a popular protocol because it’s open-source. Open-source software allows you flexibility in configuring the protocol to meet your needs.
• SSTP: Microsoft developed the Secure Socket Tunneling Protocol (SSTP). Unsurprisingly, it works best with Windows computers. It’s considered on par with OpenVPN, but its primary downside is that it’s not open-source software.
• PPTP: The Point-to-Point Tunneling Protocol (PPTP) is one of the oldest, originally developed for dial-up connections. It’s widely available but only offers weak security.
• L2TP/IPSec: The Layer Two Tunneling Protocol (L2TP) is a successor to PPTP. It’s used with the Internet Protocol Security (IPSec) network protocol suite and has seen wide adoption for its strength and reliability, but it’s slower than other VPN protocols.
• IKEv2/IPSec: The Internet Key Exchange version two (IKEv2) combines with the IPSec protocol suite for strong security. It maintains a stable VPN connection when you switch between Wi-Fi and mobile cell networks, making it popular for use with mobile devices.
• WireGuard: This is a newer protocol, and some consider it the future of VPN protocols because it offers both a fast internet connection and strong security.
3. VPN software installation
Once you’ve assessed your business needs, sign up with a VPN provider who can deliver what you’re seeking. Look for providers who offer plans geared for businesses, such as TunnelBear.
Once you’ve signed up with a VPN provider, download their VPN software, called a client, onto your devices. This software is what sets up the encryption protection for your online activities, providing access to the provider’s servers. Some vendors offer other features, such as an ad blocker.
The initial software installation lets you configure your administrator VPN settings. This establishes the settings used by all endpoints, and the VPN provider’s software will walk you through the setup steps.
4. Test and troubleshoot
Once you’ve set up security parameters, test your new VPN on a handful of devices before rolling it out to staff. The VPN software might conflict with other software you’re currently using, so testing before a full rollout is a must to work out any issues.
If issues crop up, ensure you’re using the latest version of any software on the computer. Update all software to the latest versions. Also, try different VPN protocols to see if that solves the problem.
5. Rollout
After you’ve resolved any setup issues, have your team install the VPN on their machines. Usually, the VPN provider’s software setup process involves a link for staff to download the VPN software client.
Fine-tune your VPN system after rollout. Define a default VPN server to connect to automatically. Usually, the server closest to your location is best for speed.
You may also want to implement a kill switch if your VPN provider offers this. The kill switch will cut off internet access if the VPN becomes disconnected.
4 key benefits to using a VPN
A VPN delivers several business benefits that offset its one major detractor: slower internet speeds. These four are among a VPN’s biggest advantages.
1. Security
One of the top VPN benefits is better security. The encrypted tunnel ensures no criminal can access your data.
A VPN is critical if you’re using a public Wi-Fi network such as the ones found at coffee shops. These networks offer internet access but no security to protect you from cybercriminals, making a VPN mandatory.
2. Privacy
The biggest benefit afforded by a VPN is online privacy. You’re using the VPN server’s IP address, preventing prying eyes, such as the websites you visit and even your ISP, from seeing your identity.
3. Remote access
If you have staff spread across different locations, a VPN allows them to connect online as though you were all in the same office. This makes sharing files and accessing company data convenient and safe, protecting remote workers from hackers.
4. Circumvent censorship
Several online restrictions exist, ranging from blocking access to specific content to government censorship of entire websites based on your geographic location. If you travel for business, these blocks can affect you when you least expect it.
Since a VPN masks your actual device and uses the location of the VPN server, you can circumvent these blocks by making it seem as though your internet traffic is coming from the geographic location of the server.
How to select the right VPN for you
Not all VPN providers can fulfill your needs. To choose the best VPN solution, prioritize your list of needs and benefits.
Use your prioritized list to find a VPN vendor who can at least meet your top requirements. Consider these factors.
• Privacy: If online privacy is paramount, go beyond a typical VPN setup and choose a multihop VPN instead.
• Protocols: You’ll want to verify the available VPN protocols used by a vendor. If a VPN vendor offers only the PPTP protocol, I recommend moving on to another provider with stronger security protocols.
• Simultaneous connections: The number of simultaneous connections is important. It defines how many devices can connect to your VPN simultaneously. You’ll want to account for this number as part of your VPN selection process.
• VPN servers: The number and location of VPN servers are another consideration. A vendor with lots of VPN servers spread around the world can help you avoid traffic bottlenecks that slow down your internet speeds.
Last advice about how to set up a VPN
A VPN for computers is not a cure-all for internet threats. See it as a single component of your overall internet security, not the only one you use.
Cyberattacks come in many forms, including through emails that a VPN won’t block. So you’ll still require comprehensive antivirus software to protect against these threats. You should also have a system in place where you routinely back up your business data.
By adding a VPN to your company’s digital security, you’ve established a solid foundation for protecting your staff, company, and customer data from the rising threat of cybercrime.
The post How to Set Up a VPN for Small Businesses appeared first on The blueprint and is written by Robert Izquierdo
Original source: The blueprint






